Table of contents
NICE EnginFrame is a feature-rich and very versatile portal framework dedicated to VDI session and HPC job and data management. You can find more information here.
The script below automatically installs NICE EnginFrame on Redhat/CentOS 6.x, 7.x and 8.x and an existing SLURM cluster and targets a single node installation. You can build and install SLURM with our automatic SLURM installation script. By using this script you accept the EnginFrame EULA. To install EnginFrame you need a trial license which you can request here. Further information can be found in the EnginFrame Quick Start Guide. In case of multi-node visualization please make sure the directory /opt/nice/enginframe/sessions/ is shared among all nodes and users are know on all nodes.
After the EnginFrame installation part the script shows how to enable SSL for EnginFrame using Apache. The EnginFrame installation jar comes with an easy to use installation wizard as well which supports the integration of schedulers like SGE, LSF, PBSPro/OpenPBS, Torque, … as well as the DCV Session Manager for VDI so please feel free to try those in addition. The EF installation wizard creates the config-file which has been embedded below into the installation script to configure EnginFrame.
DCV Session Manager Setup
In case you use another scheduler than the DCV Session Manager to schedule VDI session on Windows and Linux you can skip this part.
To allow EnginFrame to interact with DCV Session Manager, you need to register EnginFrame as a Session Manager API client (EF is the sample client name here) which provides us with the client-id and password:
# dcv-session-manager-broker register-api-client --client-name EF
client-id: 5ee022b4-9307-4a08-bebb-0320c716cc9d
client-password: OGMzYTk5MDgtODNjNC00Y2U4LTg2ODEtZDFmMmZjMzRjMDk5
In the EnginFrame installation configuration we need to enter the respective Session Manager information which is then stored in the file $EF_TOP/conf/plugins/dcvsm/clusters.props (permission 600) as example for Session Manager cluster dcvsm_cl1 with Session Manager host sm-host (we use the default port 8443 for client to broker communication, or in case we adapted it to 8448 we replace 8443 with 8448):
# cat $EF_TOP/conf/plugins/dcvsm/clusters.props
DCVSM_CLUSTER_dcvsm_cl1_AUTH_ID=5ee022b4-9307-4a08-bebb-0320c716cc9d # example
DCVSM_CLUSTER_dcvsm_cl1_AUTH_PASSWORD=OGMzYTk5MDgtODNjNC00Y2U4LTg2ODEtZDFmMmZjMzRjMDk5 # example
DCVSM_CLUSTER_dcvsm_cl1_AUTH_ENDPOINT=https://sm-host:8443/oauth2/token
DCVSM_CLUSTER_dcvsm_cl1_SESSION_MANAGER_ENDPOINT=https://sm-host:8443
DCVSM_CLUSTER_dcvsm_cl1_NO_STRICT_TLS=true
where dcvsm_cl1 is the name of the Session Manager cluster as stored in $EF_TOP/conf/plugins/dcvsm/dcvsm.efconf:
DCVSM_CLUSTER_IDS=dcvsm_cl1
EnginFrame Installation Script
You can execute the script at once (download EnginFrame Installation Script) or step by step to monitor the execution of the single steps:
################################################################################
# Copyright (C) 2019-2020 NI SP GmbH
# All Rights Reserved
#
# info@ni-sp.com / www.ni-sp.com
#
# We provide the information on an as is basis.
# We provide no warranties, express or implied, related to the
# accuracy, completeness, timeliness, useability, and/or merchantability
# of the data and are not liable for any loss, damage, claim, liability,
# expense, or penalty, or for any direct, indirect, special, secondary,
# incidental, consequential, or exemplary damages or lost profit
# deriving from the use or misuse of this information.
################################################################################
# Version v1.2
#
# Script to perform the automatic installation of NICE EnginFrame on Redhat/CentOS servers and SLURM cluster
# Targets a single node installation
# check if running on RH/CentOS
rhce="`hostnamectl | grep Operating | egrep -i 'centos|redhat'`"
if [ "$rhce" == "" ] ; then
echo Exiting as only Redhat/CentOS are supported by this script at the moment
exit
fi
echo
echo Checking for latest EnginFrame version
echo
efdownload=`curl --silent --output - https://download.enginframe.com/ | grep href | grep enginframe/packages | grep jar | sed -e 's/.*http/http/' -e 's/jar.*/jar/'`
echo "We will be downloading EnginFrame from $efdownload ..."
# download EF
# -nv
wget $efdownload
# sudo yum install java
sudo yum install jre
sudo adduser efnobody
# ######
# sudo adduser dcvtest
# sudo passwd dcvtest
EFADMIN=efadmin
echo "Creating user $EFADMIN (EnginFrame admin user)"
# if you prefer another user please adapt the config below
sudo useradd $EFADMIN
# sudo passwd $EFADMIN
# sudo java -jar enginframe-202*-r*.jar
# find JRE
JREVAR=""
if [ -h /etc/alternatives/jre ] ; then
JREVAR=/etc/alternatives/jre
else
JREVAR=`ls /usr/lib/jvm/jre* |head -1 | sed -e 's/://'`
fi
# check for absolute license file path
if [ -f license.ef ] ; then
LICENSEF="`/bin/pwd`"/license.ef
echo Using license $LICENSEF
else
echo "Could not find EnginFrame license file license.ef in local directory ... exiting"
exit
fi
cat > efinstall.config << EOF
######################################################################
# EnginFrame
#
# This file has been automaticaly generated on Sat Nov 28 22:50:50 EST 2020
######################################################################
efinstall.config.version = 1.0
######################################################################
# License Agreement
# Review the license terms before installing EnginFrame
######################################################################
# Setting the property ef.accept.eula to 'true' you declare that you have read
# you have read all the terms of the EnginFrame
# license agreement and that you accept them.
#
# Values: [true|false]
ef.accept.eula = true
######################################################################
# What's new in EnginFrame 2020.0
######################################################################
######################################################################
# License File
# Install the license file
######################################################################
# License file
# kernel.eflicense = /root/license.ef
kernel.eflicense = $LICENSEF
######################################################################
# Choose Install Location
# Choose the directory in which to install EnginFrame
######################################################################
# Install directory
nice.root.dir.ui = /opt/nice
######################################################################
# EnginFrame Update
# Preliminary Checks
######################################################################
######################################################################
# Components to install
# The list of what will be installed
######################################################################
# EnginFrame
#component_enginframe = true
# EnginFrame
#component_enginframe_finalizer = true
# EnginFrame Kernel
#component_kernel = true
# EnginFrame Applets
#component_applets = true
# Include Parser Library
#component_parser = true
# EnginFrame HTTP Authentication Plug-in
#component_http = true
# EnginFrame PAM Authentication Plug-in
#component_pam = true
# EnginFrame LDAP Authentication Plug-in
#component_ldap = true
# EnginFrame ActiveDirectory Authentication Plug-in
#component_activedirectory = true
# EnginFrame RSS Feed Supplier Plug-in
#component_rss = true
# EnginFrame LSF Grid Integration Plug-in
#component_lsf = true
# PBS Plug-in
#component_pbs = true
# Torque Plug-in
#component_torque = true
# Grid Engine Plug-in
#component_sge = true
# SLURM Plug-in
#component_slurm = true
# AWS Batch Plug-in
#component_awsbatch = true
# DCV Session Manager Plug-in
#component_dcvsm = true
# EnginFrame Demo Portal
#component_demo = true
# NEUTRO Grid Plug-in
#component_neutro = true
# EnginFrame VDI Portal
#component_vdi = true
# EnginFrame Applications Portal
#component_applications = true
# Service Manager Plug-in
#component_service-manager = true
# User Group Manager Plug-in
#component_user-group-manager = true
######################################################################
# Java Runtime Environment (JRE) Selection
# Define which JRE will be used by EnginFrame
######################################################################
# JRE base directory
# kernel.java.home = /usr/lib/jvm/java-1.8.0-openjdk-1.8.0.272.b10-1.el8_2.x86_64/jre
kernel.java.home = $JREVAR
######################################################################
# EnginFrame Spoolers
# Choose the location for the EnginFrame spoolers
######################################################################
# Spoolers directory
ef.spooler.dir = /opt/nice/enginframe/spoolers
######################################################################
# EnginFrame Repository
# Choose the location for the EnginFrame repository
######################################################################
# Repositories directory
ef.repository.dir = /opt/nice/enginframe/repository
######################################################################
# EnginFrame Sessions
# Choose the location for the EnginFrame sessions
######################################################################
# Sessions directory
ef.sessions.dir = /opt/nice/enginframe/sessions
######################################################################
# EnginFrame Data
# Choose the location for the EnginFrame data directory
######################################################################
# Data directory
ef.data.root.dir = /opt/nice/enginframe/data
######################################################################
# EnginFrame Logs and Temp
# Choose the location for the EnginFrame logs and temp directories
######################################################################
# Logs directory
ef.logs.root.dir = /opt/nice/enginframe/logs
# Temp directory
ef.temp.root.dir = /opt/nice/enginframe/tmp
######################################################################
# EnginFrame configuration
# Choose the EnginFrame configuration
######################################################################
# Choose the EnginFrame configuration:
# Values: [PRO|ENT]
#ef.product = HPC PRO
######################################################################
# EnginFrame Agent
# Choose if EnginFrame Agent will run on this machine
######################################################################
# EF Agent will be started on this machine
# Values: [true|false]
kernel.agent.on.same.machine = true
######################################################################
# Agent Configuration
# Configure the EnginFrame agent communication
######################################################################
# TCP port on which the RMI registry listens for requests
kernel.agent.rmi.port = 9999
# TCP port on which the EnginFrame agent listens for RMI requests from the EnginFrame server
kernel.agent.rmi.bind.port = 9998
######################################################################
# Agent Configuration
# Configure the EnginFrame agent communication
######################################################################
# Hostname where the agent will be launched
#kernel.agent.host =
# TCP port on which the RMI registry listens for requests
#kernel.agent.rmi.port = 9999
# TCP port on which the EnginFrame agent listens for RMI requests from the EnginFrame server
#kernel.agent.rmi.bind.port = 9998
######################################################################
# EnginFrame Administrator
# Specify the EnginFrame administrator
######################################################################
# EnginFrame administrator
kernel.ef.admin.user = efadmin
######################################################################
# Apache Tomcat HTTPS
# Enable Apache Tomcat HTTPS
######################################################################
# Apache Tomcat with HTTPS
# Values: [true|false]
kernel.server.tomcat.https = false
######################################################################
# Apache Tomcat Configuration
# Configure Apache Tomcat
######################################################################
# OS user owning the Apache Tomcat process
kernel.ef.tomcat.user = efnobody
# Context of the EnginFrame web application
kernel.ef.root.context = enginframe
# TCP port on which Apache Tomcat listens for HTTP connections
kernel.tomcat.port = 8080
# TCP port on which Apache Tomcat listens for shutdown requests
kernel.tomcat.shutdown.port = 8005
######################################################################
# Apache Tomcat Configuration
# Configure Apache Tomcat
######################################################################
# OS user owning the Apache Tomcat process
#kernel.ef.tomcat.user = efnobody
# Context of the EnginFrame web application
#kernel.ef.root.context = enginframe
# TCP port on which Apache Tomcat listens for HTTPS connections
#kernel.tomcat.https.port = 8443
# TCP port on which Apache Tomcat listens for shutdown requests
#kernel.tomcat.shutdown.port = 8005
# Hostname to be set into the autogenerated certificate for Apache Tomcat
#kernel.server.tomcat.https.ef.hostname = cent8
######################################################################
# EnginFrame Database Configuration
# Configure EnginFrame Database
######################################################################
# Select database to use
# Values: [derby|other-db]
kernel.ef.db = derby
######################################################################
# EnginFrame Database Configuration
# Configure EnginFrame Database
######################################################################
# DerbyDB port
kernel.ef.derby.db.port = 1527
######################################################################
# EnginFrame Database Configuration
# Configure EnginFrame Database
######################################################################
# JDBC URL
#kernel.ef.db.url = jdbc\:derby\://localhost\:1527/EnginFrameDB
# Username
#kernel.ef.db.admin.name = dbadmin
# Property hidden PasswordTextInput
#kernel.ef.db.admin.password = XXXXXXXX
######################################################################
# Enterprise Configuration
# Configure Enterprise features
######################################################################
# Comma separated list of server IPs and ports e.g. 192.168.0.1:7800,192.168.0.2:7800
#kernel.ef.enterprise.tcp.servers =
######################################################################
# EnginFrame Startup
# Choose whether EnginFrame should start at boot
######################################################################
# Start EnginFrame at boot
# Values: [true|false]
kernel.start_enginframe_at_boot = true
######################################################################
# EnginFrame Startup
# Select the version to start
######################################################################
# Use the new version?
# Values: [true|false]
#kernel.update_current_version = true
######################################################################
# EnginFrame Developer's Documentation
# Choose whether to install the technical showcase and documentation
######################################################################
# Do you want to install the EnginFrame Developer's Documentation?
# Values: [true|false]
demo.install = false
######################################################################
# Authentication Manager
# Select the default authentication manager
######################################################################
#
# Values: [pam|http|ldap|activedirectory|certificate]
default.auth.mgr = pam
######################################################################
# EnginFrame Certificate Authority Configuration
# Configure EnginFrame Certificate Authority
######################################################################
# Get username from client certificate
# Values: [true|false]
#kernel.authorization.certificate.userCertificate = false
######################################################################
# Authentication Manager Configuration
# Specify the PAM service
######################################################################
# PAM service
pam.service = system-auth
######################################################################
# Authentication Manager Configuration
# Test the PAM authentication manager
######################################################################
# Username
pam.user = dcvtest
# Property hidden PasswordTextInput
#pam.userpw = XXXXXXXX
######################################################################
# Authentication Manager Configuration
# Specify the 'ldapsearch' location
######################################################################
# Location of 'ldapsearch'
#ldap.ldapsearch = /usr/bin/ldapsearch
######################################################################
# Authentication Manager Configuration
# Specify the information needed to query the LDAP server
######################################################################
# Name of the host on which the LDAP server is located
#ldap.server =
# TCP port on which the LDAP server listens for requests
#ldap.port = 389
# Does the LDAP server require a secure connection (TLS)?
# Values: [true|false]
#ldap.secure = false
# Use simple authentication (instead of SASL)
# Values: [true|false]
#ldap.simple.auth = true
# Default base Distinguished Name (example: 'ou=People,dc=nice')
#ldap.base =
######################################################################
# LDAP Plug-in Configuration
# Specify username and password to test authentication
######################################################################
# Username
#ldap.user =
# Property hidden PasswordTextInput
#ldap.userpw = XXXXXXXX
######################################################################
# Authentication Manager Configuration
# Specify the 'ldapsearch' location
######################################################################
# Location of 'ldapsearch'
#activedirectory.ldapsearch = /usr/bin/ldapsearch
######################################################################
# Authentication Manager Configuration
# Specify the information needed to query the ActiveDirectory server
######################################################################
# Name of the host on which the ActiveDirectory server is located
#activedirectory.server =
# TCP port on which the ActiveDirectory server listens for requests
#activedirectory.port = 389
# Does the ActiveDirectory server require a secure connection (TLS)?
# Values: [true|false]
#activedirectory.secure = false
# Default base Distinguished Name
#activedirectory.base =
######################################################################
# ActiveDirectory Plug-in Configuration
# Specify username and password to test authentication
######################################################################
# Bind as
#activedirectory.bindas =
# Property hidden PasswordTextInput
#activedirectory.bindpwd = XXXXXXXX
# Username
#activedirectory.user =
# Property hidden PasswordTextInput
#activedirectory.userpw = XXXXXXXX
######################################################################
# Grid Manager
# Select the grid managers
######################################################################
#
ef.jobmanager = slurm
######################################################################
# LSF/OpenLava Integration
# Configure EnginFrame to integrate with LSF/OpenLava
######################################################################
# Shell profile file
#lsf.profile.file = /opt/lsf/conf/profile.lsf
######################################################################
# LSF/OpenLava Integration
# Configure EnginFrame to integrate with LSF/OpenLava
######################################################################
# Shell profile file
#lsf.profile.file = /opt/lsf/conf/profile.lsf
######################################################################
# PBS Integration
# Configure EnginFrame to integrate with PBS
######################################################################
# PBS binaries path
#pbs.binaries.path = /usr/pbs/bin
######################################################################
# Torque Integration
# Configure EnginFrame to integrate with Torque
######################################################################
# Torque binaries path
#torque.binaries.path = /usr/torque/bin
######################################################################
# Grid Engine Integration
# Configure EnginFrame to integrate with Grid Engine
######################################################################
# Grid Engine shell profile file
#sge.profile.file = /opt/sge/default/common/settings.sh
######################################################################
# SLURM Integration
# Configure EnginFrame to integrate with SLURM
######################################################################
# SLURM binaries path
slurm.binaries.path = /usr/bin
######################################################################
# AWS Batch Integration
# Configure EnginFrame to integrate with AWS Batch
######################################################################
# AWS ParallelCluster name
#awsbatch.cluster = batch
# AWS ParallelCluster region
#awsbatch.region = us-east-1
######################################################################
# NEUTRO Plug-in
# Configuration of NEUTRO connection
######################################################################
# NEUTRO Master Address(es)
#neutro.neutro.master = localhost
######################################################################
# Delegate Interactive Session Manager
# Select the delegate interactive session managers
######################################################################
# DCV Session Manager
# Values: [true|false]
ef.delegate.dcvsm = true
######################################################################
# DCVSessionManager
# Configure DCV Session Manager connection
######################################################################
# OAuth2 Server URL
dcvsm.oauth2.url = https\://cent8\:8445/oauth2/token
# OAuth2 Client ID
dcvsm.oauth2.id = 4f25ac78-92b6-4f5e-9fdf-864f3f47dfa6
# Property hidden PasswordTextInput
#dcvsm.oauth2.psw = XXXXXXXX
# DCV Session Manager Broker URI
dcvsm.broker.url = https\://cent8\:8445/
######################################################################
# DCVSessionManager
# Configure DCV Session Manager connection
######################################################################
# Disable TLS Strict Check
# Values: [true|false]
dcvsm.no.strict.tls = true
######################################################################
# Do not modify any configuration below this line
######################################################################
intro-targets = component_enginframe,component_kernel,component_applets,component_parser,component_http,component_pam,component_ldap,component_activedirectory,component_rss,component_lsf,component_pbs,component_torque,component_sge,component_slurm,component_awsbatch,component_dcvsm,component_demo,component_neutro,component_vdi,component_applications,component_service-manager,component_user-group-manager,component_enginframe_finalizer,
progress-targets = cleanuptarget,
EOF
sudo java -jar enginframe-202*.jar --batch -f efinstall.config
echo "=================================="
echo Finished installing EnginFrame ...
echo "=================================="
sleep 3
cd /opt/nice/enginframe/bin
./enginframe start
# /opt/nice/enginframe/2019.0-r915/enginframe/plugins/interactive/lib/remote
sudo iptables-save
sudo firewall-cmd --zone=public --add-port=8080/tcp --permanent
sudo firewall-cmd --zone=public --add-port=443/tcp --permanent
sudo firewall-cmd --reload
sudo firewall-cmd --list-all
sudo iptables-save | egrep "8080|443"
echo
echo
echo Now EnginFrame should be up and running ...
echo You can connect with your browser at `hostname`:8080
echo
echo We exit here ... "(have a look at the script below to see how to e.g. enable SSL for EnginFrame)"
echo
echo
exit
# covered by DCV
# yum install tigervnc-server
# vncserver
# install WM
# sudo yum install xfwm4 -y
echo Login as EF Admin and publish the interactive services in the Views portal
# X is running
# export XAUTHORITY=/run/user/42/gdm/Xauthority; export DISPLAY=:0
# xhost +
systemctl start dcvserver
dcv create-session --owner dcvtest t2
# https://support.nice-software.com/support/solutions/articles/1000053839-enginframe-https-with-httpd
# enable HTTPS for EF
yum install httpd mod_ssl -y
cat > /etc/httpd/conf.d/httpd-enginframe.conf << EOF
<Location "/enginframe">
ProxyPass ajp://127.0.0.1:8009/enginframe flushpackets=on
</Location>
EOF
export EF_CONF_ROOT="/opt/nice/enginframe/conf"
# uncomment AJP section in $EF_CONF_ROOT/tomcat/conf/server.xml to look like this:
# <Connector port="8009"
# enableLookups="false"
# redirectPort="8443"
# protocol="AJP/1.3"
# tomcatAuthentication="false"
# />
vim $EF_CONF_ROOT/tomcat/conf/server.xml
cat >> $EF_CONF_ROOT/enginframe/agent.conf << EOF
ef.download.server.url=http://127.0.0.1:8080/enginframe/download
EOF
systemctl enable httpd.service
export EF_TOP="/opt/nice/enginframe"
$EF_TOP/bin/enginframe stop
service httpd stop
sleep 6
$EF_TOP/bin/enginframe start
service httpd start
###################################################################
###################################################################
# startup script to adapt IPs
localIP="`hostname -s`"
# adapt SLURM.conf
if [ "`grep $localIP /etc/slurm/slurm.conf | head -1`" == "" ] ; then
cat /etc/slurm/slurm.conf | gawk -v LIP=$localIP '
{ # gensub(regexp, replacement, how [, target]) #
b = gensub (/ip-[0-9\\-]*/, LIP, "g");
print b;
}
' > SLURM.conf.TMP
sudo mv SLURM.conf.TMP /etc/slurm/slurm.conf
sudo service slurmd stop
sudo service slurmctld stop
sleep 3
sudo service slurmctld start
sudo service slurmd start
fi
# exit
extip=`curl --silent ifconfig.me`
if [ "`grep $localIP /opt/nice/enginframe/conf/plugins/interactive/nat.conf`" == "" ] ; then
echo $localIP $extip >> /opt/nice/enginframe/conf/plugins/interactive/nat.conf
exit
fi
# config extip in nat.conf
cat /opt/nice/enginframe/conf/plugins/interactive/nat.conf | gawk -v IP=$extip -v LIP=$localIP '
{if ( $1 != LIP )
print $0;
else
print LIP" " IP
}' > nat.conf.TMP
sudo mv nat.conf.TMP /opt/nice/enginframe/conf/plugins/interactive/nat.conf
exit
# setup slurm ip in case image has been moved so hostname is different
127.0.0.1 localhost localhost.localdomain localhost4 localhost4.localdomain4
::1 localhost localhost.localdomain localhost6 localhost6.localdomain6
172.31.23.201 node1
172.31.23.202 node2
172.31.23.203 node3
172.31.23.204 node4
172.31.23.205 node5
The EnginFrame installation script can be downloaded here as well:
Enabling EnginFrame Views Desktop Services
After a new installation of EnginFrame you might want to enable the Linux or Windows Desktop service. Here are the steps – first login to the “Virtual Desktop/Views” portal as EF Admin user:
Then click on “Admin’s Portal” to the upper right:
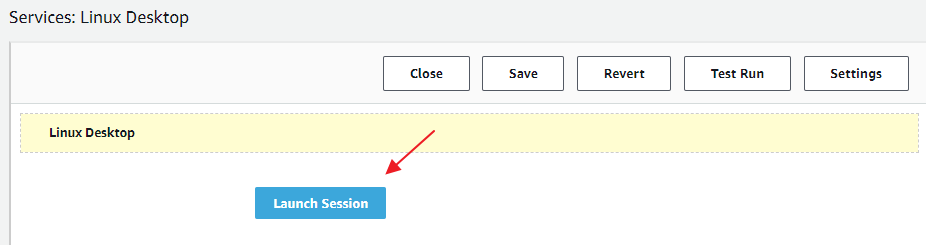
and then click on “Interactive Services” in the left menu:

Click on the blue link of service you want to enable – e.g. “Linux Desktop” and then in the Service Editor on the “Launch Session” Button:
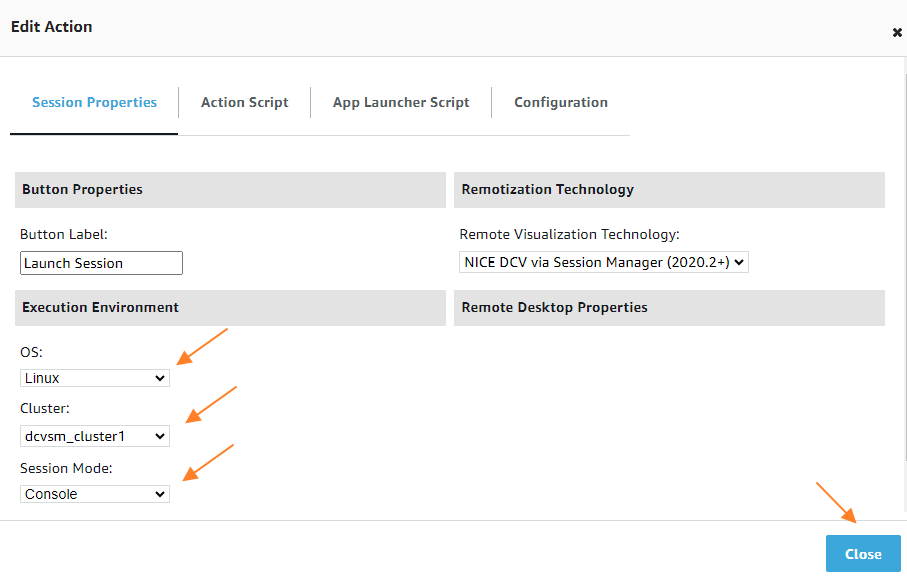
In the configuration you can configure and verify your OS, the Cluster to use and the Session Mode. Then click “Close” to confirm the values:
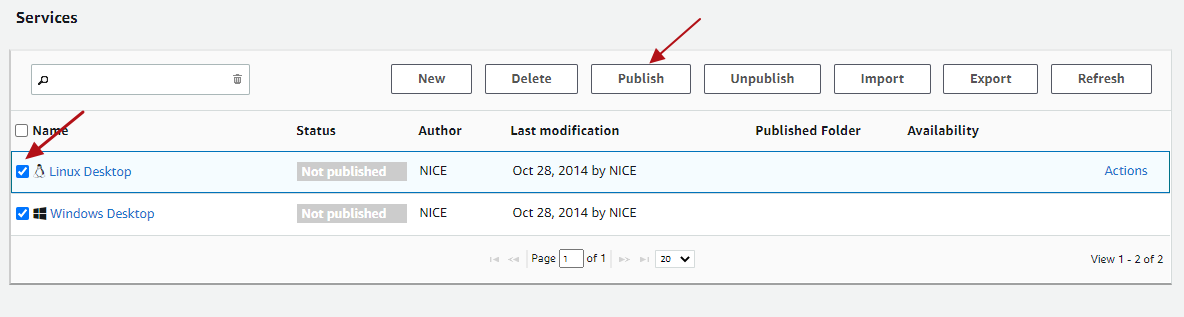
As next step you can “Save” and “Close” the service editor and you will see the services overview where you then can select and “Publish” the respective desktop services:
Switch to “User View” in the upper right and you can see the new service enabled in the left menu.
Configuring NICE DCV to use External Authentication of the DCV Session Manager Broker
With EnginFrame Views Single-Sign-On (SSO) you can login to the DCV session automatically. EF Views will create a session token which is then verified by DCV using the Auth Token Verifier of NICE DCV Session Manager (SM) Broker.
In case of NICE DCV on Windows the configuration is in the registry. You can copy the broker self-signed CA to C:\Program Files\NICE\DCVSessionManagerAgent\conf\dcvsmbroker_ca.pem. For the auth-token-verifier please specify the URL for the token verifier on the Broker replacing the hostname in the example below:
REM Settings example
REM HKEY_USERS/S-1-5-18/Software/GSettings/com/nicesoftware/dcv/security/auth-token-verifier = https://ip-172-31-4-230:8445/agent/validate-authentication-token
REM HKEY_USERS/S-1-5-18/Software/GSettings/com/nicesoftware/dcv/security/ca-file = C:\Program Files\NICE\DCVSessionManagerAgent\conf\dcvsmbroker_ca.pem
REM HKEY_USERS/S-1-5-18/Software/GSettings/com/nicesoftware/dcv/security/no-tls-strict = 1
REM Powershell:
New-ItemProperty -Path "Microsoft.PowerShell.Core\Registry::\HKEY_USERS\S-1-5-18\Software\GSettings\com\nicesoftware\dcv\security" -Name auth-token-verifier -PropertyType STRING -Value "https://ip-172-31-4-230:8445/agent/validate-authentication-token" -Force
New-ItemProperty -Path "Microsoft.PowerShell.Core\Registry::\HKEY_USERS\S-1-5-18\Software\GSettings\com\nicesoftware\dcv\security" -Name ca-file -PropertyType STRING -Value "C:\Program Files\NICE\DCVSessionManagerAgent\conf\dcvsmbroker_ca.pem" -Force
New-ItemProperty -Path "Microsoft.PowerShell.Core\Registry::\HKEY_USERS\S-1-5-18\Software\GSettings\com\nicesoftware\dcv\security" -Name no-tls-strict -PropertyType DWORD -Value 1 -Force
In case of NICE DCV on Linux you can configure external authentication in /etc/dcv/dcv.conf (for ca-file, please specify the path to the broker’s self-signed CA copied to the host previously. For auth-token-verifier, specify the URL for the token verifier on the Broker replacing the hostname example below):
[security]
administrators=["dcvsmagent"]
ca-file="/etc/dcv-session-manager-agent/dcvsmbroker_ca.pem"
no-tls-strict=true
auth-token-verifier="https://ip-172-31-4-230:8445/agent/validate-authentication-token"
After the configuration please restart the DCV server. Any questions just let us know. Read more about NICE DCV.
