EC2 License
In case you are using DCV in AWS EC2 you need to allow access to an S3 bucket. Otherwise you will e.g. see the following indicator in the top bar of your DCV HTML5 client.
First you should create an access role and policy to enable the permissions in your IAM.
As next step your EC2 instance needs to be associated with the role. In the webconsole this is done by right-click on respective instance (or choose Actions from the upper menu) to show the following pop-up after hovering above “Instance Settings” and then click on “Attach/Replace IAM Role”:
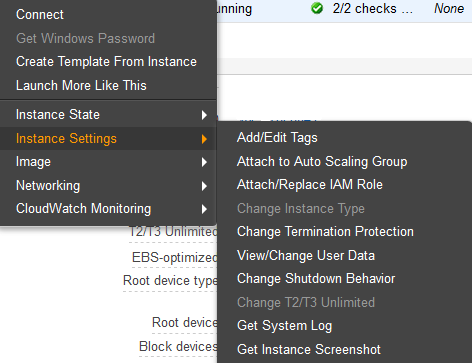
Select your role and click on “Apply”
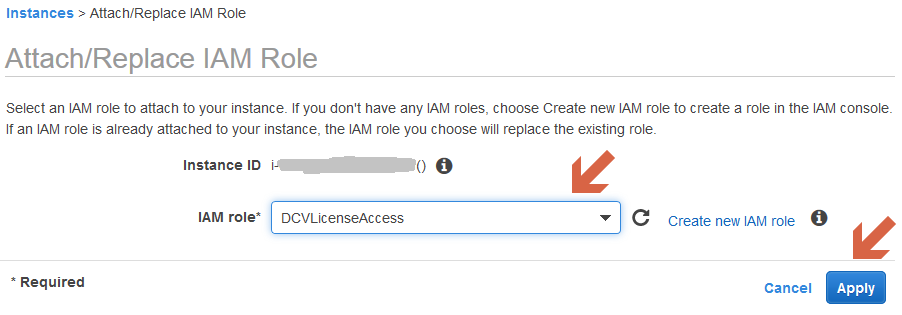
If everything is correct the indicator for the missing DCV license should disappear automatically after the next periodical check of the DCV server.
The same can be achieved on the command line as well with the AWS CLI:
aws iam create-instance-profile --instance-profile-name DCVLicProfile
# replace the role name with your role name
aws iam add-role-to-instance-profile --role-name DCVLicenseAccess --instance-profile-name DCVLicProfile
# be sure to have your region configured correctly
# you can check for instances with the following command
aws ec2 describe-instances --query 'Reservations[].Instances[].[PrivateIpAddress,InstanceId,Tags[?Key==`Name`].Value[]]' --output text | sed '$!N;s/\n/ /'
# attach the IAM role to the instance
aws ec2 associate-iam-instance-profile --instance-id YOUR_INSTANCE_ID --iam-instance-profile Name=DCVLicProfile
# check the association
aws ec2 describe-iam-instance-profile-associationsPlease feel free to use our contact form for any questions or comments.
EC2 License (stored in S3 bucket)
This guide explains how to setup access to the DCV license in AWS EC2. In AWS EC2 instances NICE DCV can be used for free. This is enabled by periodically accessing a S3 bucket containing the license. To access the S3 bucket we need to configure an AWS IAM role and policy.
Have a look at the end of the article for an alternative approach using the command line with the AWS CLI instead of the web console.
Creating the IAM role
Our example uses eu-west-1 as AWS region – please adapt accordingly.
- Open https://console.aws.amazon.com/iam/home?region=eu-west-1#/roles
- Click on “Create role”
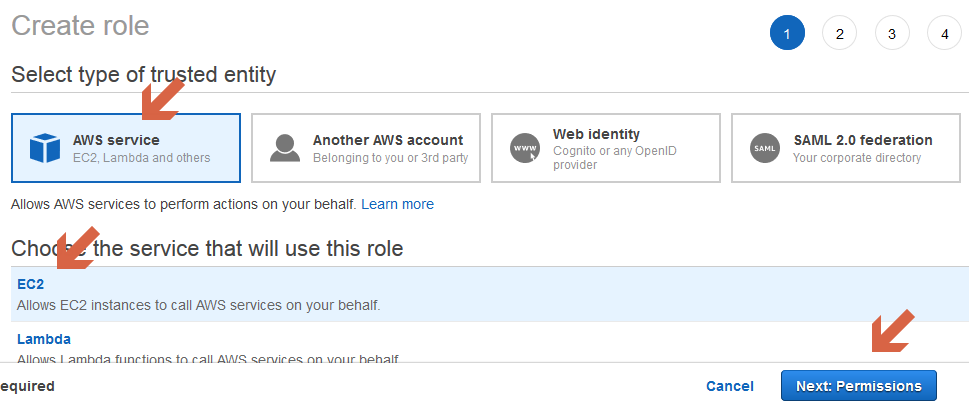
- On the next page
- Select “AWS service”
- Select “EC2”
- Click on “Next: Permissions”
- On the next page click on “Next: Tags” to move forward
- On the next page click on “Next: Review” to move forward
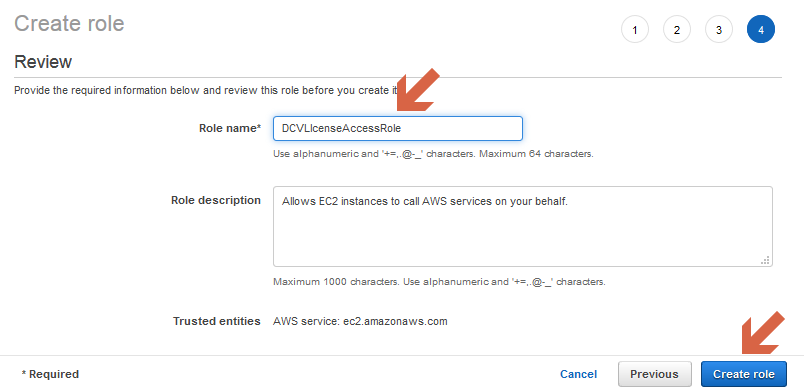
- On the next page enter the name for your role and click “Create role”
Creating the IAM policy
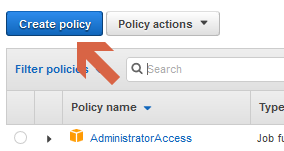
- Click on Policies in the left menu
- Click on “Create policy”
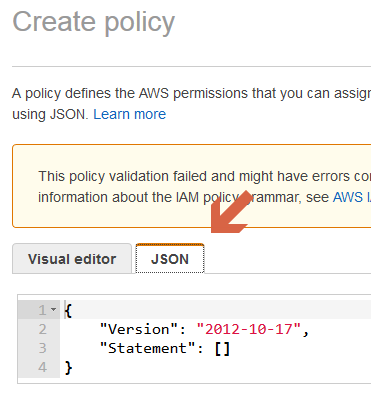
- On the next page click on “JSON”
- Insert the code below into the JSON field replacing the existing code – please replace the region with your region:
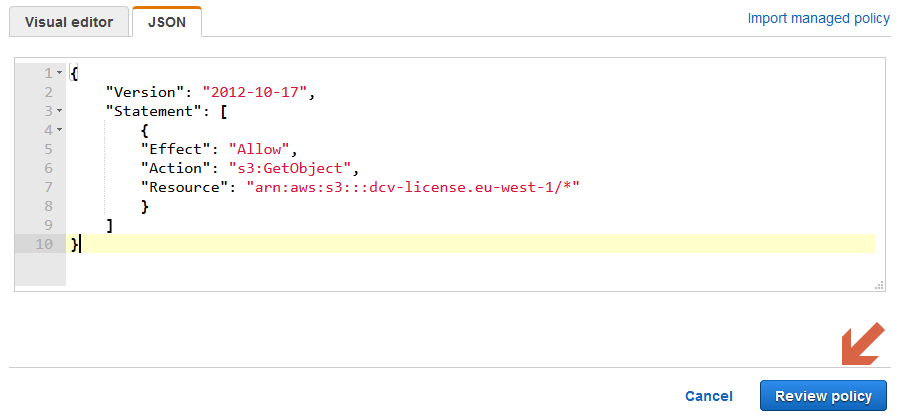
- Enter the name for the policy and click “Create policy”
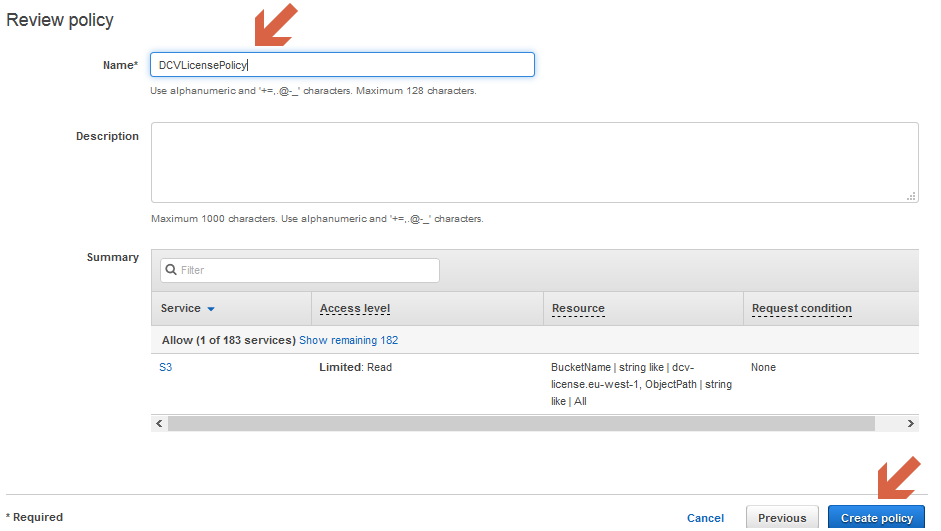
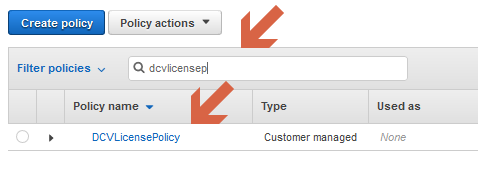
Search for your new policy and click on it to open it
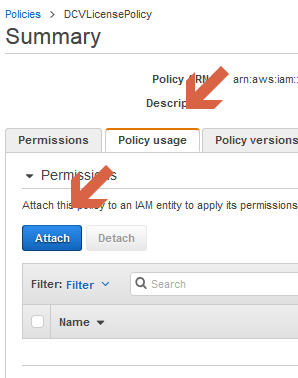
Click on “Policy usage” and then on “Attach”
Enter your DCV policy name, select the policy and click on “Attach policy”
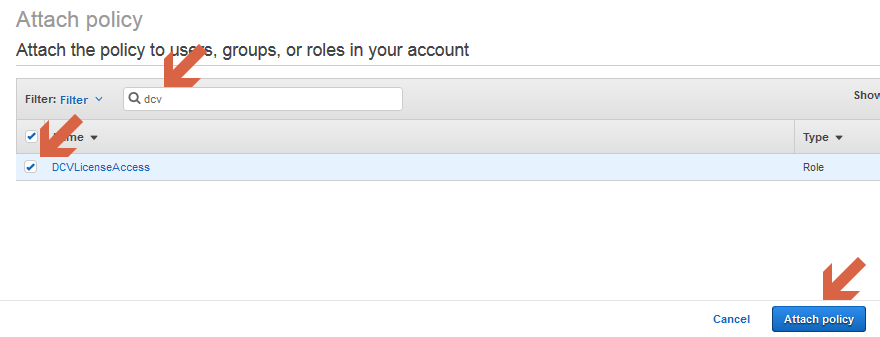
You are done! Your new DCV role and policy has been created. The next step is to use it and attach it to the instance running DCV.
Alternative – Use the AWS CLI commandline to configure DCV License role and policy
Create the role
cat <<< '{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": {
"Service": "ec2.amazonaws.com"
},
"Action": "sts:AssumeRole"
}
]
}' > ROLE.json
aws iam create-role --role-name DCVLicenseAccess --assume-role-policy-document file://ROLE.jsonCreate the policy (please remember to replace the region):
# Replace region (here eu-west-1) with your EC2 region
cat <<< '{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": "s3:GetObject",
"Resource": "arn:aws:s3:::dcv-license.eu-west-1/*"
}
]
}' > POL.json
aws iam create-policy --policy-name DCVLicenseAccess --policy-document file://POL.json
# REMEMBER THE ARN of the DCV license access policy in the output
aws iam attach-role-policy --role-name DCVLicenseAccess --policy-arn {YOUR_ARN} # e.g. arn:aws:iam::ACCOUNT_NR:policy/DCVLicenseAccess
# verify the role policy
aws iam list-attached-role-policies --role-name DCVLicenseAccess
# REMOVE json files
rm POL.json ROLE.json
# to remove a policy
# aws iam detach-role-policy --role-name DCVLicenseAccess --policy-arn arn:aws:iam::ACCOUNT_ID:policy/DCVPlease feel free to use our contact form for any questions or comments.



